Understanding security testing for SQL Server environments
Security testing is the process of determining whether or not a system is secure. This can be done by compromising various security measures, such as applications, databases, or systems. It can also be done by creating test cases that destabilize a system’s security checks. In order to understand all of the security measures, we need to take at various layers in the SQL Server environment, let’s first understand what they are.
Security Layers for SQL Server
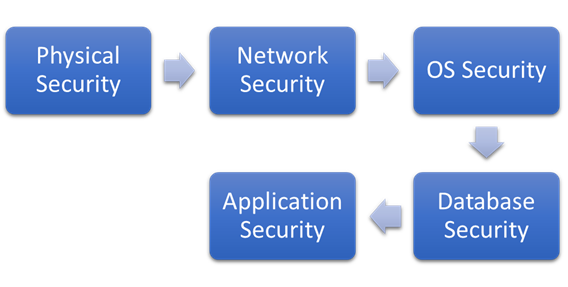
To safeguard and protect its instances and databases, we can split SQL Server security into several tiers. These layers might include the following:
• Physical security
• Network security
• Operating system security
• Database security
• Application security
Physical security is the most important layer as it protects all other layers. If an attacker can physically access the system, they can bypass all other security measures. That’s why physical security is crucial for SQL Server systems.
Network security is the next layer of security. If an attacker can access the network, they can potentially bypass other security measures. That’s why it’s important to have a secure network infrastructure and properly configure SQL Server networking.
• Every unneeded connection is cut off.
• External network traffic is blocked by firewall rules.
• All network endpoints are protected through encryption or third-party tools.
• Every packet that passes through the networks is encrypted.
• First, undergo a vulnerability assessment to discover any holes in the network or software that could be exploited by external attackers.
Operating system security is the third layer of security. The operating system is the foundation of the SQL Server environment. If an attacker can compromise the operating system, they can potentially take control of the entire system.
That’s why it’s important to harden the operating system and properly configure SQL Server.
• All unneeded services and protocols are disabled.
• All unneeded user accounts are removed.
• Permissions and privileges are properly configured.
Database security is the fourth layer of security. If an attacker can access the database, they can potentially view or modify sensitive data. That’s why it’s important to properly secure the database.All unneeded user accounts are removed.Permissions and privileges are properly configured.
The database is kept up to date with the latest security patches.The database is backed up regularly.
Application security The last stage is where we concentrate on securing the connection to the database server and preventing unauthorized remote code executions. We also keep an eye out for SQL Injection attacks, which identify these threats and assist us in defending against any harmful code that may be injected into your application program.
There are various third-party tools available that you can use to configure the measures mentioned above. These tools will help you automate and optimize your website so that it runs more smoothly and efficiently.
Now that we’ve reviewed all of the security precautions and policies necessary to safeguard our database environment, we’ll move on to discussing security testing. We’ll attempt to compromise our systems and databases in order to identify flaws in them.
Security testing in SQL Server
The section above covered the basics of securing databases and systems. However, it is not enough to simply apply these measures–you must also regularly test them to make sure they are effective.
It is possible to find a lot of holes and vulnerabilities in an application. Such flaws are identified by security testing, which helps us discover potential security gaps and exploits and then repair them on time. It also aids in keeping the databases’ SLAs alive by detecting risks and remediating them as needed.
Furthermore, keep in mind that security testing is a process that takes up quite a bit of time and money. Just like we have various security measures implemented at multiple layers, as defined earlier, we should test for policy compliance at each layer. These layers are the same ones that were defined in the previous section.
• Physical security
• Network security
• Operating system security
• Database security
• Application security
Physical security testing it is important to regularly audit your security systems and keep proper documentation. Make sure to lock all premises where systems are hosted, and follow best practices for physical security. This will help safeguard against fire, flood, theft, or any man-made disasters.
As part of its testing, you can plan the below steps:
• Do not enter the data center room without proper access, or you will be removed.
• To assure the building’s safety against fire, earthquakes, or human-made catastrophes, practice mock drills.
• Assure that all security personnel pay attention by attempting to cross a security barrier.
• It is advisable to install cameras throughout the data center in order to monitor all activities.
Network security testing is important to protect your devices and data from outside attacks. It involves scanning ports to find any open or unprotected access points, looking for vulnerabilities that could be exploited, checking passwords for weak spots, and making sure multi-factor authentication is properly set up.
You can test for these things using Qualys, Acunetix, NMAP, Wireshark, and other tools. During this testing process, we must make sure to cover:
• Vulnerability scanning allows you to find any security flaws in your system so you can fix them before anyone takes advantage of them.
• Check every port for possible signs of hacking.
• Checking the security of a computer system or network by simulating an attack
• Auditing who can access what on your property
Ensure to take remediations of all risks or loopholes identified during the above security testing.
Operating System security testing involves scanning the system for security vulnerabilities, detecting intruders, checking configurations and policies, and auditing access control management.
Testing comes under this layer is:
• Vulnerability scanning and risk assessment are the first steps in any security plan.
• By trying to tamper with system settings, we can make sure that any possible configurational issues have been dealt with.
• To verify that uninvited access is impossible, we conduct intruder detection testing.
• Passwords are frequently cracked with weak algorithms.
• We should try to use generic accounts so that we can remove all the other non-generic accounts from the system.
Database security testing The same actions we discussed for operating systems apply to databases as well. In addition, access control management is used to review database authentication or authorization configurations. Data protection measures, such as encryption, should also be employed, and unwanted features and services should be disabled in order to reduce the surface area for attackers.
• Attempt to establish connections with the database instance or databases by a variety of tools, other logins present in the system such as service accounts, using generic accounts like sa, port numbers, or by compromising weak passwords.
• In order to test for data vulnerabilities, try accessing database objects which other users should not have access to.
• To ensure that no one has unnecessary higher access or unused logins, audit access management.
• To try and get information that has been coded
• Make sure you don’t have any additional components installed in your SQL Server.
Application security testing This layer is responsible for establishing and maintaining secure connections to the database system to prevent attacks through SQL Injections. We may use third-party tools like SQLMap or SQLNinja to do this testing. These programs will assist us in detecting security flaws that an external attacker can exploit to insert malicious SQL codes into system calls (SQL Injections) at the application level.
If you have any questions about security testing for SQL Server environments, please don’t hesitate to contact Access Database Development. We would be more than happy to answer any of your questions and help you get started on the right path to keeping your data safe and secure.
